Physical Security Design Consulting
An ideal building or facility protective system:
• Deters
• Detects
• Defends against
• Defeats Aggressors
The primary design objectives are defense (delay and shielding) and detection
(sense, assess, and communicate aggression)
The main focus in site design is improving detection, adding delay, and providing defense from some threats through standoff
Minimum Measures for Site Design are:
- Clear zone - eliminate potential hiding places to improve site visibility
- Maximize standoff from the outer perimeter and parking areas
- Eliminate roadways or drives that approach perpendicular to a building
- Minimize the number of access points to the facility
- Avoid parking under a facility
- Provide adequate security lighting
- Reduce or avoid vantage points
Defense-in-Depth is the preferred method of Security Design.
- For many threats and tactics the best defense if standoff.
- In addition, you can minimize risk and increase your chances of success by
layering your defense.
- Each layer presents an opportunity to add detection or delay elements to foil an
adversary.
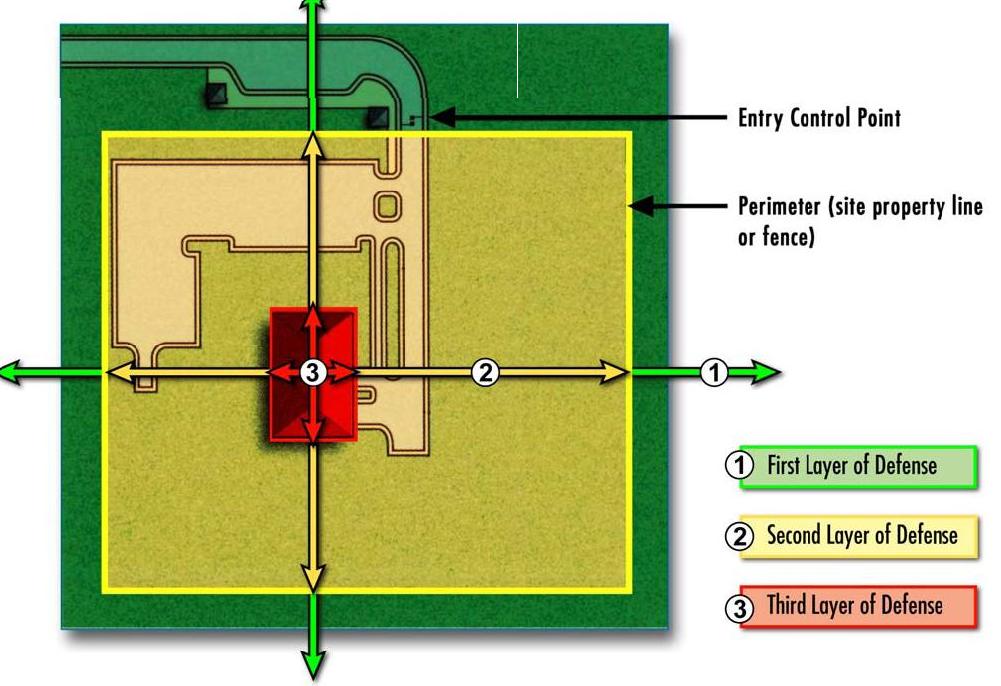
Source FEMA 428
Let us review your site design plans for assesment of your site security
posture and improvement needs. We will review specific tactics followed by
suggestions on how to mitigate that tactic possible impact.
To receive your Physical Vulnerability Assessment, please submit your payment of $999.00
B E T T E R: Please submit your payment of $1999.00 for a complete Physical Vulnerability Assessment or Design covering a single location.
| 

