1. Transportation Security
2. Bridge and Tunnel Assessments
3. Highway Assessments
|
 |
Step 5 - General guidelines to calculate the range of costs for implementing the selected countermeasures
In this step, general guidelines are provided to calculate the range of costs for implementing the selected countermeasures
The countermeasures identified in Step 4 are intended to deter or detect a potential or real attack or to help defend critical assets in the event
an attack is underway. In some cases, the countermeasure will be an action taken to deny access to an asset through physical features or enforcement
strategies; in other cases, countermeasures will render the attack harmless or mitigate damages. In many cases, combinations of countermeasures will be
needed to achieve the desired vulnerability reduction. This first step in cost estimation is to “package” countermeasures in ways that make sense
operationally and from a vulnerability reduction perspective. In some cases, a single measure will apply to multiple assets (e.g., video surveillance
may cover multiple transportation assets in high density urban areas); in others, multiple countermeasures will be applied to a single asset (e.g., the
vulnerability of a critical bridge or tunnel may be reduced by applying electronic security for intrusion detection as well as physical barriers to deny
access to critical structural elements).
Determine acquisition, operation, and maintenance cost of proposed countermeasures The capital investment and annual operation and maintenance costs
for countermeasures for each highway agency varies widely. It is beyond the scope of this Guide to provide a detailed description of life cycle cost
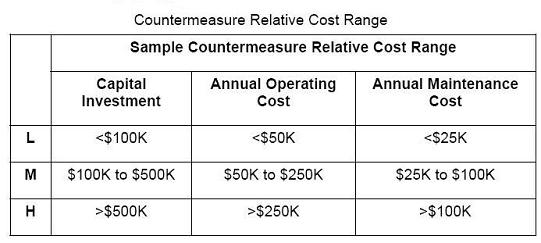
estimation. Nevertheless, the following table provides a tool for assigning preliminary costs to each countermeasure listed in this Guide. These costs
are described as high (H), medium (M) or low (L). The relative ranges associated with high, medium, and low costs are very subjective and depend on many
variables. Sample values are provided in the Table as a general guide to categorizing the countermeasure costs.
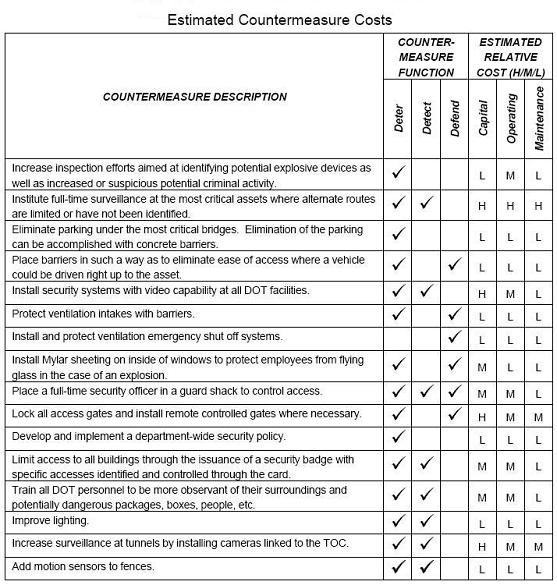
Apply costs to assets. This step is the simple application of the unit cost of the countermeasure packages
to the critical assets. State DOTs can group
assets by asset type (similar to the categories listed in step 1) and extend the unit price for appropriate countermeasures to the number of critical
assets in each category. For example, assume a State DOT has identified ten high priority bridges (in terms of their criticality and vulnerability) and
the unit cost for the countermeasure package (e.g., intrusion detection, access denial or control, surveillance methods) selected for reducing bridge
vulnerability. This unit cost can be applied to the ten critical bridges, recognizing that acquisition, installation, and operation and maintenance may
vary from bridge to bridge but the overall cost estimate will provide a reasonable estimate to support investment decisions. A similar process applies to
other asset types (e.g., inspection facilities, traffic operations centers) where other countermeasure packages will be applied. Once countermeasure costs
have been determined, a strategy must be developed for procuring and implementing the countermeasures. This will most likely require cost benefit analyses
and trade off studies, as State DOT budgets are often limited. However, stress should be placed on immediate procurement action, to eliminate or reduce
vulnerabilities as quickly as possible.
To receive your Draft Vulnerability
Assessment , please submit your payment of $1999.00
|

