Step 2 - Identify critical assets.
- Characterize threat
Threat characterization for the purposes of vulnerability assessment is different from what might be used on a day-to-day
basis as part of an operational security plan
"Although threat information is deemed beneficial to the [assessment], it should not be given undue weight. There remains
insufficient empirical data on domestic terrorist activity to suggest a pattern of particular targeting of a specific region
or city. Henceforth, it must be recognized that the identification of a particular threat is not an absolute predictor that
a terrorist incident will occur.”
The Bush Administration established the “Homeland Security Advisory System” to improve coordination and communication among
all levels of government and the American public in the fight against terrorism. This system provides a national framework for
communicating the nature and degree of terrorist threats between government
officials and the citizens they represent. At this
time, the system uses a variety of factors to assess the threat, such as:
- Is the threat credible?
- Is the threat corroborated?
- Is the threat specific and/or imminent?
- How grave is the threat?
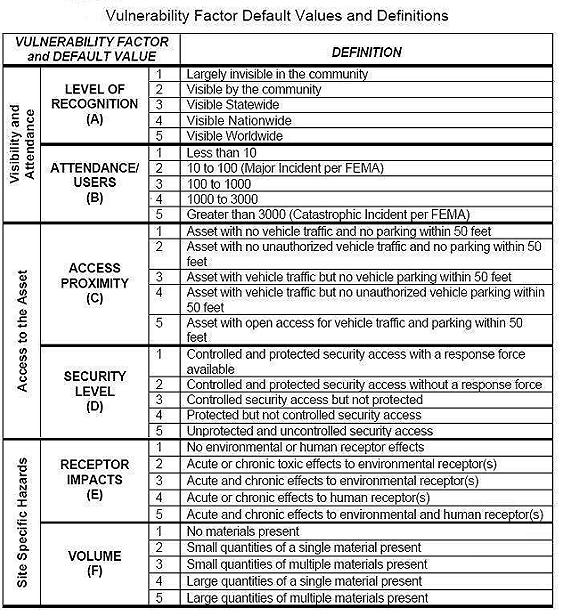
- Identify exposure levels, by assigning vulnerability factors to the critical assets
- Visibility and Attendance - Awareness of the existence of the asset and the number of people typically present
- Access to the Asset - The availability of an asset to ingress and egress by a potential threat element
- Site Specific Hazards - The presence of materials that have biological, nuclear, incendiary, chemical, or explosive properties
in quantities that would expend initial response capabilities if compromised
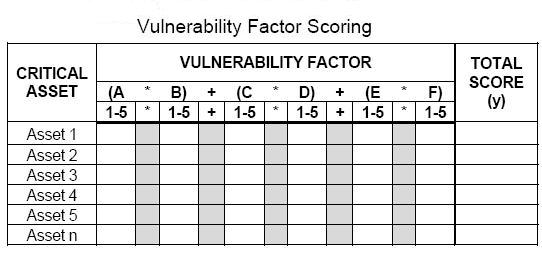
- Score asset vulnerability
The following formula is used to calculate the vulnerability factor (y) for
each critical asset.
In the formula, the sub-elements are multiplied by each other for visibility and attendance (A * B),
for access to the asset (C * D), and for site specific hazards (E * F).
The three resulting numbers are then added.
Vulnerability Factor (y) = ( A * B ) + ( C * D ) + ( E * F )
For any critical asset, the lowest attainable vulnerability factor score is 3 and the highest attainable score is 75.
The vulnerability factor (y) will be used to calculate the vulnerability coordinate (Y) in the next step, as follows:
Vulnerability Coordinate: (Y) = (y/75)* 100
To receive your Draft Vulnerability
Assessment , please submit your payment of $1999.00
| 

